Host-based intrusion detection system (HIDS) for checking the integrity of files.
Advanced Intrusion Detection Environment (AIDE) is a host-based intrusion detection system (HIDS) for checking the integrity of files. It does this by creating a baseline database of files on an initial run, and then checks this database against the system on subsequent runs. File properties that can be checked against include inode, permissions, modification time, file contents, etc……….. more at archwiki📚
According to the definition, AIDE only checks for the integrity of file but not for rootkits and logs for other suspicious activities.
But there are other HIDS tools that can do this for you. Like, Splunk and OSSEC.
AIDE have provided a pretty simple documentation to undertand and get familiar with it.
How to install it?
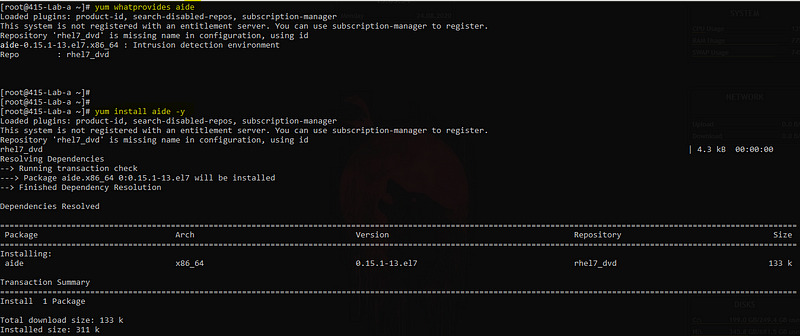
# Check what repo will provide you aide tool.
yum whatprovides aide
# And then install it, if available.
yum install aide -y
Next step ..??
Let’s check the files unpacked from the aide package we just installed.
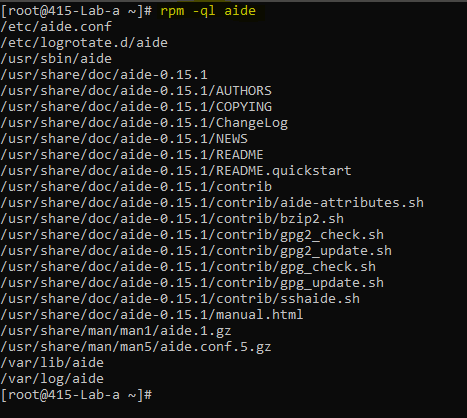
We found a configuration file — /etc/aide.conf.
# open the file with vim or your favourite text editor
vim /etc/aide.conf
# The file looked very huge so I checked its length.
wc /etc/aide.conf
# OUTPUT:
# 312 765 7333 /etc/aide.conf
Fortunately they have given a man page for the configurations settings.
man 5 aide.conf
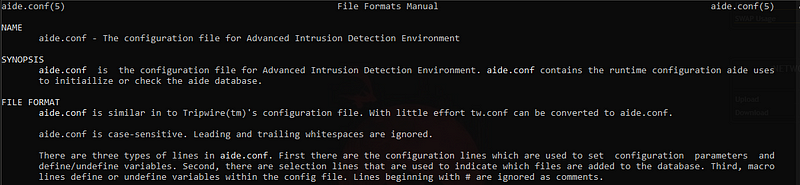
This gives me a good news. There are only 3 types of line in the configuration file.
- There are the 1️⃣configuration lines which are used to set configuration parameters and define/undefine variables.
- There are 2️⃣selection lines that are used to indicate which files are added to the database.
- 3️⃣ macro lines define or undefine variables within the config file.
- Lines beginning with # are ignored as comments.#️⃣

You can now check the config file and things will make more sense to you. Also you can check the key-value pairs from man page.
Enough for configuration… How to use it?
Go to the man page of aide.
# from terminal
man aide
Again a reminder, and I quote.
AIDE is an intrusion detection system for checking the integrity of files.
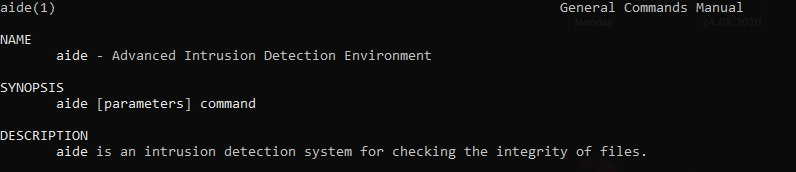
One thing to notice here is DIAGNOSTICS (Scroll down to bottom on the man page).
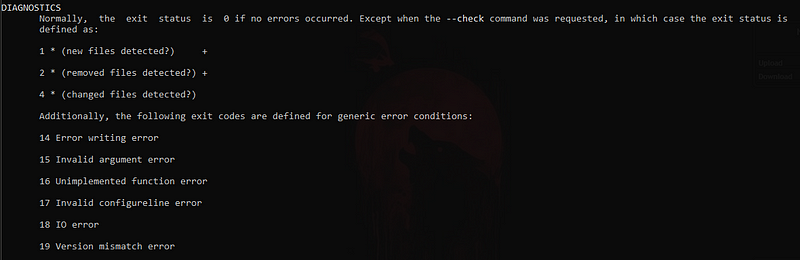
Another is, that AIDE can be controlled using few basic commands.
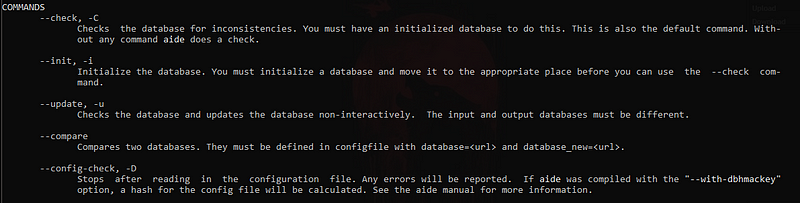
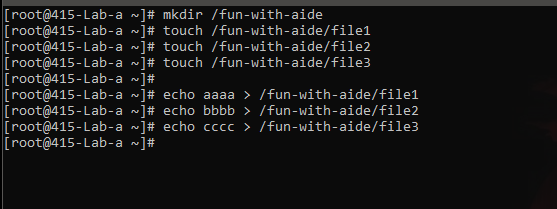
Time for some fun now!!

Game-play
- Create a folder and some files in it.
- Configure AIDE to add that folder in database.
- Have fun with the folder and files and check the AIDE logs for reports.
Adding my new folder and files to aide.conf
#-------------- My-Settings ---------------
myfilter = sha256
/fun-with-aide myfilter
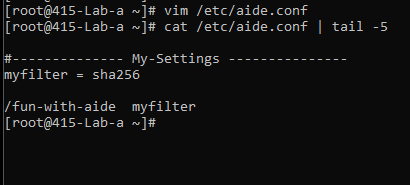
This rule is a regular expression rule and will match the complete path of any file starting from /fun-with-aide, so this will include the files inside this folder.
Now some simple steps to follow:
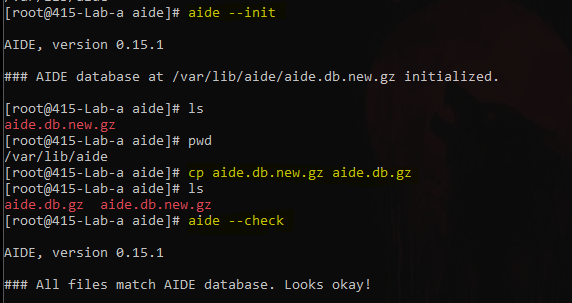
* aide --init
* cp /var/lib/aide/aide.db.new.gz /var/lib/aide/aide.db.gz
* aide --check
What if we tinker with the file /fun-with-aide/file1?
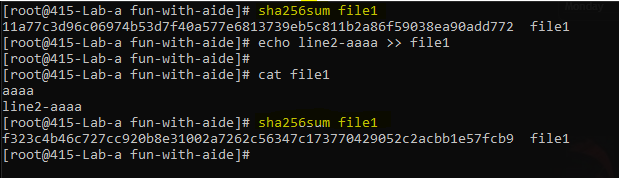
I have changed the content of the file1, due to which the sha256sum has also changed. This should be reported by aide in reports.
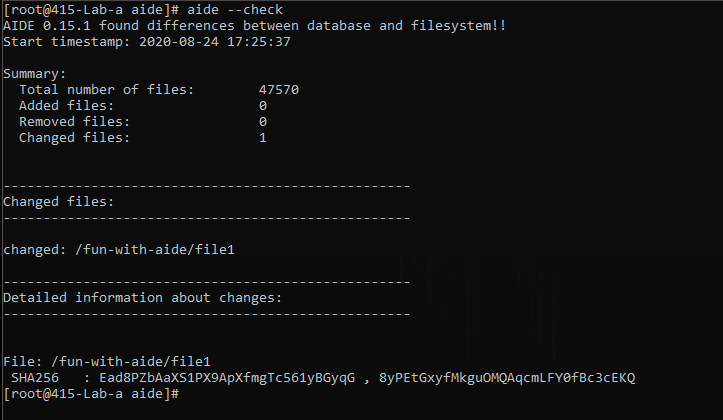
This generates a report that tells about the changes. I’ll get a count of added files, removed files and changed files, along with the name of those files and some detailed information.
AIDE can be run manually if desired, but automation is the way nowadays.

Check the below provided simple cron job script to automatically check for the changes. For more complex examples check this and this.
# SOURCE: https://wiki.archlinux.org/index.php/AIDE
#!/bin/bash -e
# these should be the same as what's defined in /etc/aide.conf
database=/var/lib/aide/aide.db.gz
database\_out=/var/lib/aide/aide.db.new.gz
if [ ! -f "$database" ]; then
echo "$database not found" >&2
exit 1
fi
aide -u || true
mv $database $database.back
mv $database\_out $database
What about if attacker changed the database??
When I checked the file type of the aide.db.gz… It came out to be a gzip compressed data, from Unix, max compression file.
This makes it very obvious to unzip this compressed file. I prefer using gunzip tool.
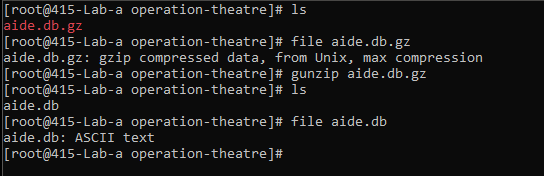
Specification of the db is also mentioned in the file.
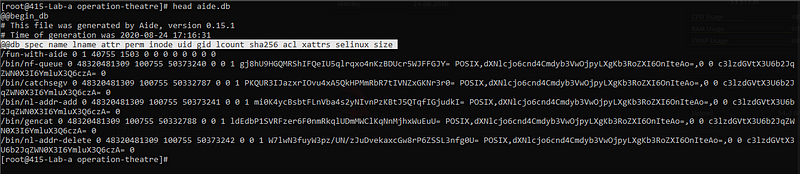
Visualizing the above in a tabular manner.
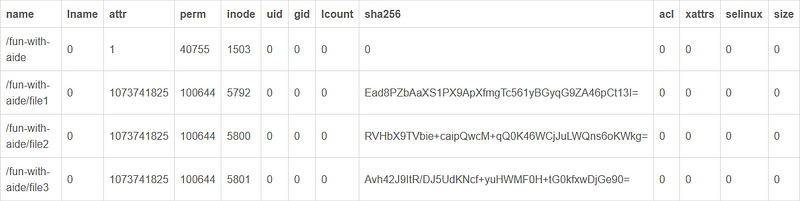
You can add more filters and integrity checks to test other things as well.

This whole db thing gives rise to a question. What if the attacker modifies the db??
Hmmm.. then he wins🤷♂️. You have to keep your db secure from attackers. For this, you should keep your database in read-only mode. So that it can be only read and no modifications can be done to this. Also you can keep the DB in a different location like in a centralized server or in a removable media like pendrive. Or you can have it your way.
You can read more about Integrity Concepts here for better security guidelines.
Conclusion
In the end, let’s understand how AIDE does what it does.
AIDE takes a “snapshot” of the state of the system, register hashes, modification times, and other data regarding the files defined by the administrator. This “snapshot” is used to build a database that is saved and may be stored on an external device for safekeeping.
When the administrator wants to run an integrity test, the administrator places the previously built database in an accessible place and commands AIDE to compare the database against the real status of the system. Should a change have happened to the computer between the snapshot creation and the test, AIDE will detect it and report it to the administrator. Alternatively, AIDE can be configured to run on a schedule and report changes daily using scheduling technologies such as cron.🔚
