Linux Unified Key Encryption — Disk Encryption
cryptsetup — manage plain dm-crypt and LUKS encrypted volumes
cryptsetup <OPTIONS> <action> <action-specific-options> <device> <dmname>
An encrypted blockdevice is protected by a key. A key is either:
- a passphrase, or
- a keyfile
What the..?
Ok.. If you are new to encryption world, then it’s time to get a bit familiar data encryption.
There are 2 methods to encrypt your data:
- Filesystem stacked level encryption : Form of disk encryption where individual files or directories are encrypted by the file system itself. read more here
- Block device level encryption : The entire partition or disk, in which the file system resides, is encrypted.

Before things go really technical and scary, let me show you how your data is stored in a harddisk.
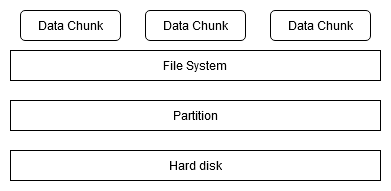
Above diagram shows how your data is stored in a harddisk.
- You create files (I am calling it data chunks) and insert your data in it.
- These files are stored in a very systematic and managed system called File System.
- Partitions are formatted to carry a file system on it.
- Harddisks are divided into Partitions. (Wanna know why? — ask Leo!)
Now when you know how your data is exactly stored in a harddisk. Let’s see how a Block device level encryption works.
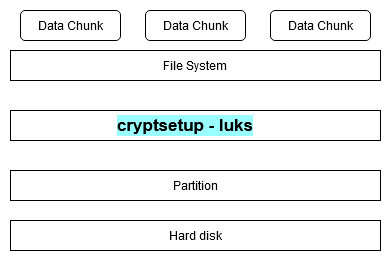
Here, a new layer is added in the usual thing.
- We attach a harddisk to our system.
- Create partitions on it.
- Encrypt the complete partition (make it password protected) 🔐
- Create filesystem (NTFS, EXT4, XFS, etc) on the encrypted partition.
- Write/save your data chunks.

Just Do It now ✔️
Installing required tools
I am using a RHEL based OS which uses yum/dnf package managers.
yum install cryptsetup -y
or
dnf install -y cryptsetup
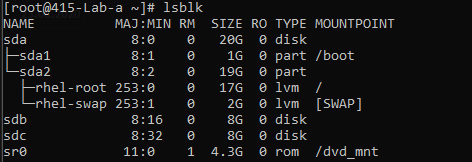
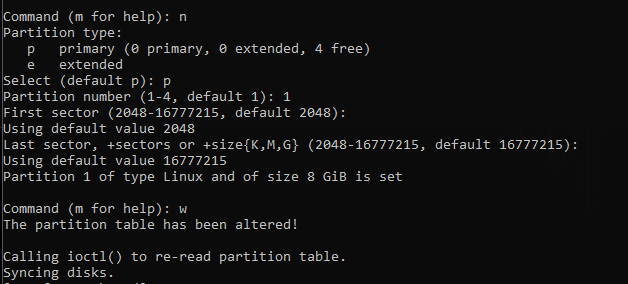
Creating the partition
lsblk - check the device name for the harddisk (sdb)
fdisk - partitioning tool
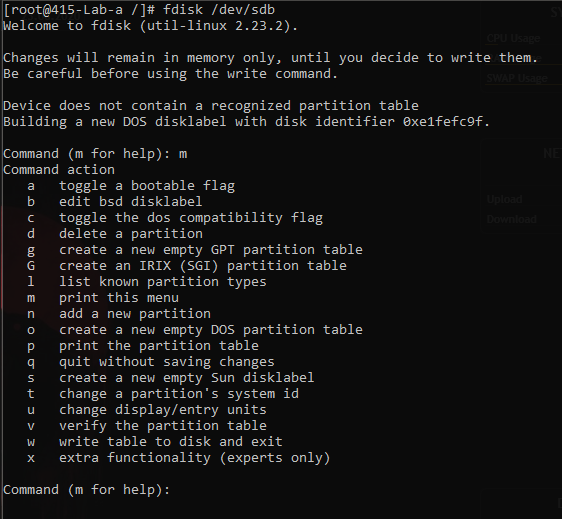
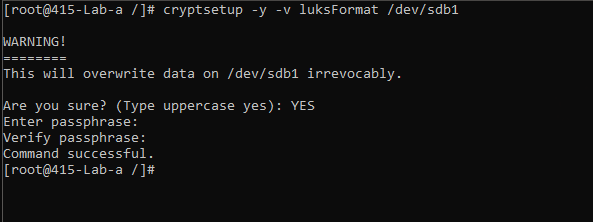
formating with luks
cryptsetup -y -v luksFormat /dev/sdb1 - encrypt the partition
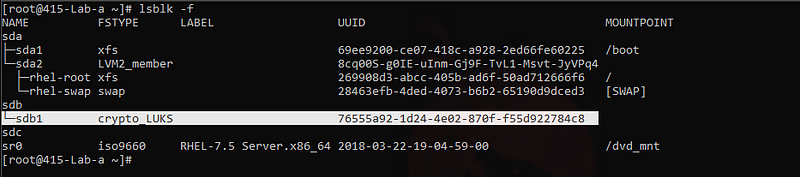
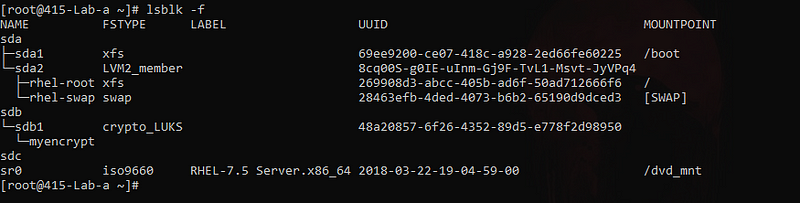
lsblk -f - check the encrypted partition
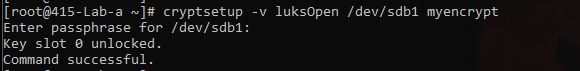
cryptsetup -v luksOpen /dev/sdb1 myencrypt - map the encrypted partition to ‘myencrypt’.
lsblk -f - check it
creating a file system
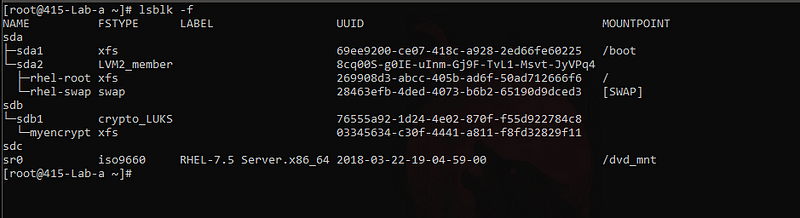
mkfs.xfs /dev/mapper/myencrypt - create a file system on top of the encrypted partition.
lsblk -f - Check the layering and filesystem associated.
creating a mountpoint
mkdir -p /mnt/my_encrypted_backup mount -v /dev/mapper/myencrypt /mnt/my_encrypted_backup/
If you face such issues - SELinux lables blah blah blah
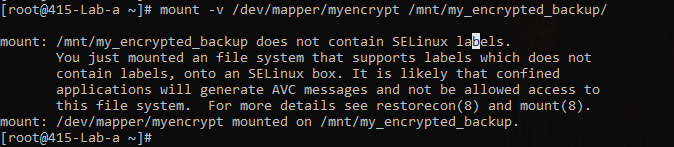
Type this on magic terminal — restorecon -vvRF /mnt/my_encrypted_backup/ - This will restore the SELinux context back to defaults for the destination directory.
Checking luks dumps
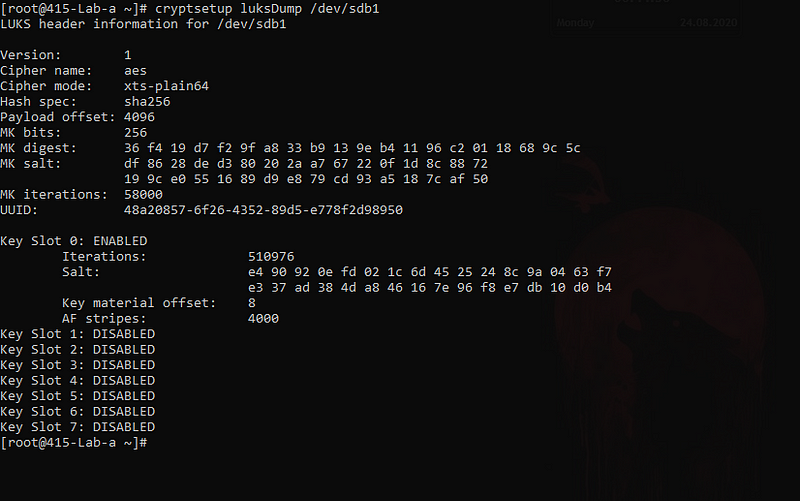
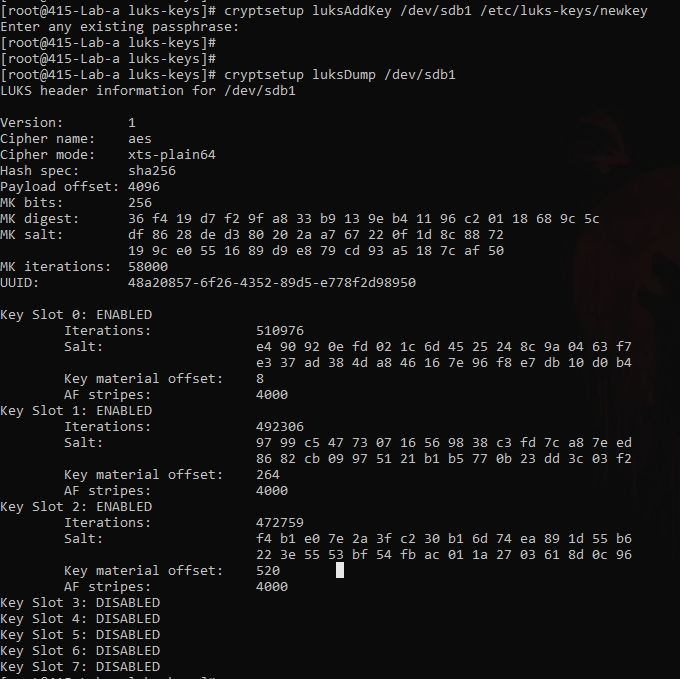
cryptsetup luksDump /dev/sdb1
Adding new key
mkdir /etc/luks-keys/; dd if=/dev/random of=/etc/luks-keys/mybackup\_key bs=32 count=1
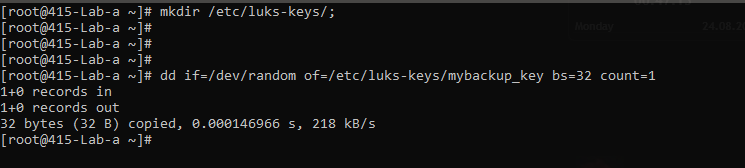
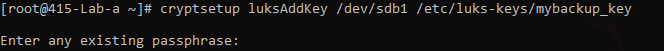
cryptsetup luksAddKey /dev/sdb1 /etc/luks-keys/mybackup\_key
Checking the dumps again
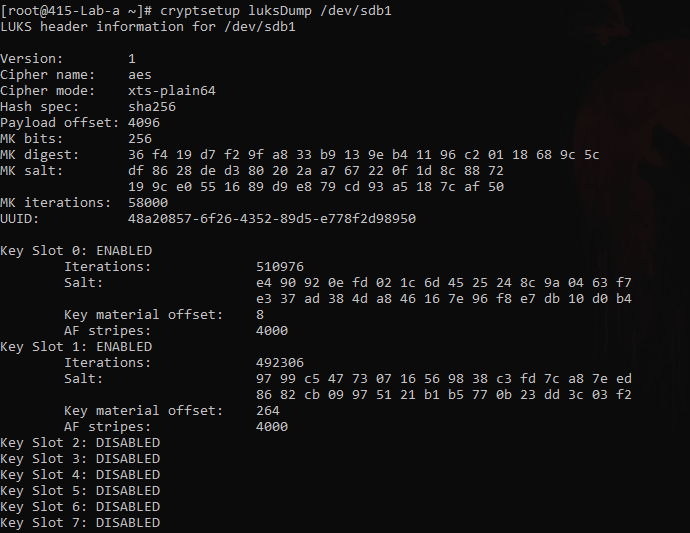
Now here are 2 slots available.
- one with the initial key I entered at the time of setting it up.
- another, just in the above step.
At this particular moment, there are few questions in my mind.

You should know them too.
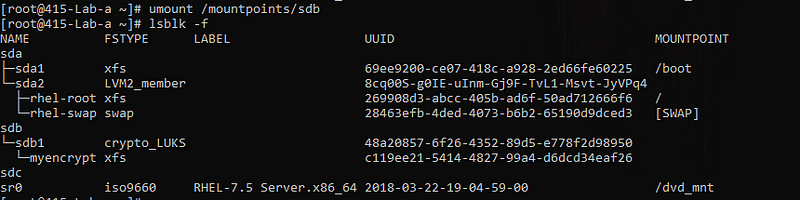
- If you want to unmount and remove the harddisk. You’ll have to follow the steps:
umount /mountpoints/sdb cryptsetup luksClose myencrypt
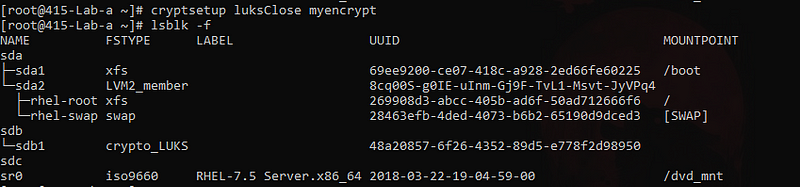
- If you want to open the luks partition with keyfile instead of the passphrase.
cryptsetup -v luksOpen /dev/sdb1 myencrypt --key-file=/etc/luks-keys/mybackup\_key
- What if someone changes the content of the keyfile?
Creating a new key
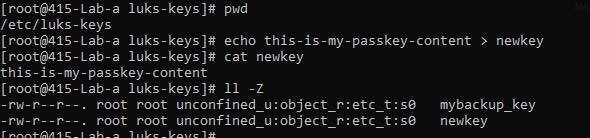
Add the key to the slots
Use key
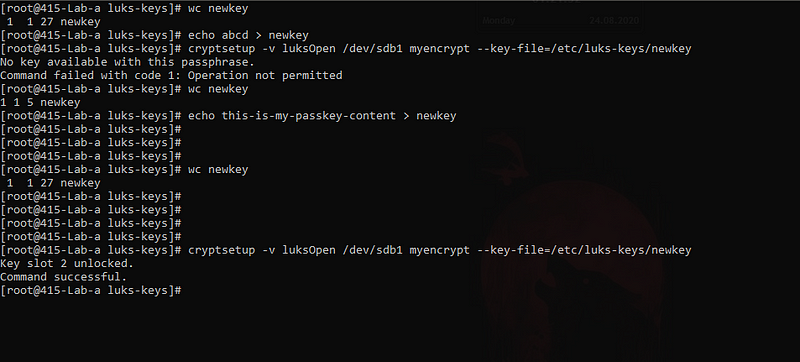
So the content inside the keyfile do matter; You can’t change it and expect things to work just fine for you.
Time for some Automation
Get the UUID of the encrypted partition
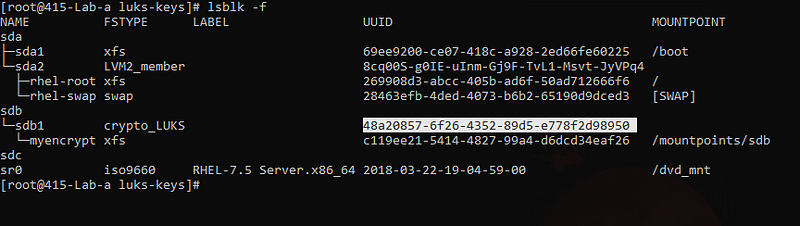
And make the below entry in /etc/crypttab file. (Check the UUID for your device - Don’t copy mine!!)
myencrypt UUID=48a20857-6f26-4352-89d5-e778f2d98950 /etc/luks-keys/mybackup\_key luks
The above line is a combination of 4 fields:
- name of the mapped device.
- uuid of the encrypted partition
- keyfile to unlock the partiotion
- type of encryption used — luks
And then make below entry in /etc/fstab file.
/dev/mapper/myencrypt /mountpoints/sdb xfs defaults 0 0
Want to learn more about crypttab and fstab
Last step to verify if the above steps worked fine or not.
- Remount and verify (using mount command with ‘a’ and ‘v’ flags for clarity)
- Reboot the system and check if everything works after reboot. (Trust me, things betray sometimes after reboot)
Want to read more about dm-crypt or device encryption?
